Password Security
Passwords are the most common method of authentication in the computer world. Therefore, it is worth knowing about how to make good passwords that prevent other people from impersonating you or stealing your information. Since we deal with sensitive information in the healthcare world, this is especially important for our industry.
Best Practices
Ideally, passwords would all be:
- Completely unique, and not reused across multiple sites or applications
- Completely random strings of characters, with upper- and lower-case letters, numbers, and symbols
- As long as possible
However, this is impractical for a number of reasons. Long passwords are difficult to remember, as are arbitrary collections of letters and numbers and symbols. And using a different password for every login multiplies the memory difficulty by the number of logins you have. So people take a number of shortcuts, each of which introduces the possibility of someone guessing or hacking your password.
Password Vulnerabilities
Each of these categories of vulnerabilities involves breaking one of the best practices above.
Password Reuse
The most common and important password vulnerability is using the same password for multiple sites. If any one of those sites is compromised by a hacker, all of the other sites should be considered compromised as well.
As an example scenario, imagine that you use the same password for online banking and for LinkedIn. Your online banking website is highly secure and difficult for hackers to attack. But LinkedIn has a vulnerability in their site and a hacker is able to figure out your LinkedIn password. Contrary to popular belief, the first thing they do once figuring out your password will not be to log into LinkedIn and hijack your account -- that would tip you off to the fact that they have stolen your password. Instead, they will try logging into other sites with more sensitive information: email, online banking, etc.
The scenario of LinkedIn being hacked is not hypothetical; it happened in June 2012.[1] Even high-profile sites often use very weak security to protect your password, so password reuse is a major vulnerability.
The ideal scenario is to use a different password for every single login. This can make your passwords extremely difficult to remember, but that will be addressed later in this article.
Weak Passwords
The most obvious instances of this are using passwords like password or your name. But password hacking algorithms are now advanced enough that users have to take other precautions as well.
Dictionary Words
Using dictionary words or proper nouns as a password has always been bad practice. When hackers are trying to guess your password, they use lists of common words as their first guesses.
Personal Information
People often use some piece of personal information
- Birth/anniversary dates/years (BobJones-7-4-1962)
- Addresses (47WellingtonSt)
- Current phone numbers (Jonathan5551212)
- Pet names (FidoDog)
The problem with currently accurate information is that many unauthorized access attempts are made by people who already know something about the potential victim.
Dr. Smith, a surgeon, may be friendly with her nurse anesthetist, Chris. Chris knows that Dr. Smith lives on Wellington St., was out of town for her son's birthday last week, has a beagle named Fido, etc. So when Chris wants to log in as Dr. Smith to see sensitive information on a celebrity patient, that personal information would be his first guesses at her password.
When using personal information as part of a password, it is better to use information that is known by as few people as possible. For example:
- Childhood pet names
- Deactivated phone numbers from many years ago
Common Obfuscation Methods
Since dictionary words are easy to remember, people often come up with a password that makes sense to them and then obfuscate the original in some way. Examples of common obfuscation methods are:
- Capitalizing the first letter (GoodDoctor)
- Appending a number, especially a year (Jane2012)
- Using multiple words together (alicehockeyfun)
- Appending symbols (pieisgood!#)
- Replacing letters with numbers[2] (myp4$$wordrule5)
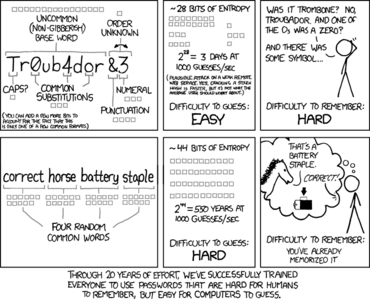
The problem with using these methods is that hackers know that people use them as well, and write password cracking algorithms that try these variations. All of these obfuscations do make passwords more difficult to guess than the unmodified versions, but they are still less secure than a completely random string of numbers and letters of the same length. The common ones (e.g., appending a recent year) are barely better than just using the rest of the password by itself.
If you are going to use obfuscation methods, try to use them in uncommon ways:
- Inserting numbers (Burger12Time) or symbols (winning!*move) into the middle
- Capitalizing a different letter instead of the first (galEnprovidEsgoOdserviCe)
Short Passwords
Even accounting for all other password best practices, a password is still relatively easy to guess if it is short. Computers are fast enough today that hackers can just try all of the possible variations until they find the correct one.[3]
Tools and Techniques
People use a number of methods to create passwords that follow best practices as much as possible. Most of these methods are tools are techniques for overcoming the shortcomings of human memory.
Password Safe Applications
A password safe is a file on a disk somewhere that stores all of your other passwords. Since this file is such an enticing target for a hacker, it must be protected very, very well.
The usual method for protecting a password safe is to encrypt the file with one very, very strong password as the encryption key. This means that you only have to commit one very difficult password to memory, and then can easily follow all of the password best practices easily.
Users of password safe applications typically use passwords that look like this: pmk+%RZ5C]o)0&DqBa4\K?):v9BX^-. Since the user does not have to actually remember any of the individual passwords, they are virtually impossible to hack.
Possible pitfalls of this method:
- Not choosing a strong enough master password. Make sure it is very, very good: 30 characters or more is ideal, with capitalization, numbers, and symbols. Since the password is so long, using dictionary words as part of it is more permissible and makes it easier to commit to memory.
- So-called "over-the-shoulder" attacks. Make sure that other people do not watch you type your password, and that you do not open your password safe on a computer that is not yours or that might be infected with viruses.
Password Generation Algorithms
Phonetic Passwords
http://stackoverflow.com/questions/624425/phonetically-memorable-password-generation-algorithms